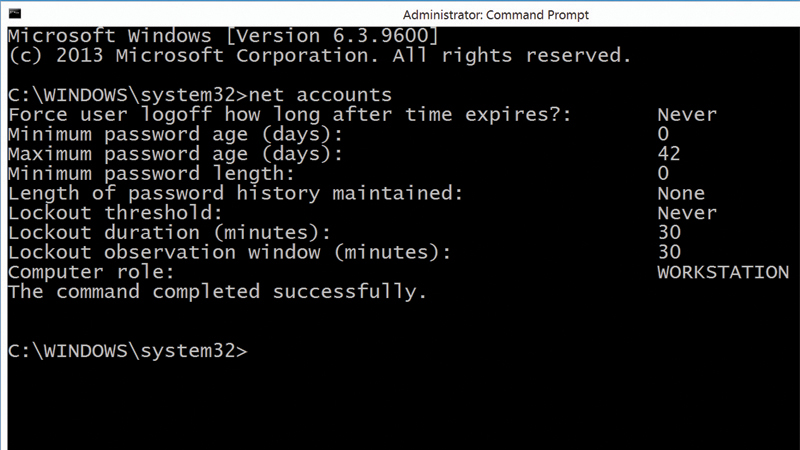
If someone is determined enough the chances are they can guess your password using brute force. Here’s how to lock down Windows following several failed login attempts. Complex passwords can be a pain to remember and prone to mistyping, but shorter passwords can be much easier to guess by brute force – trying huge numbers of passwords until the correct one is guessed. You can reduce the effectiveness of a brute force attack by limiting the number of ‘guesses’ available before the system locks the account, requiring an administrator to reset it before the user can sign in again. Also see: Best PC security software While using this policy defends against brute force attacks on passwords, it introduces another possible vulnerability, in that an attacker could cause disruption by deliberately locking multiple accounts by repeatedly trying incorrect passwords. The three local security polices you need to set are:
- Account lockout threshold, which sets the maximum number of invalid login attempts before the lockout occurs.
- Account lockout duration, which sets the time in minutes for which a lockout will remain in force. If you set this value to zero, the lock will remain until reset by an administrator.
- Account lockout window. This security policy is responsible for setting the total length of time which must pass before the count of failed login attempts is reset to zero. To set the lockout policy, open an Admin command prompt. On Windows 8.1 press Windows+X and then select Command Prompt (Admin). Next, type: Net accounts /lockoutthreshold: value Net accounts /lockoutduration: value Net accounts /lockoutwindow: value Where value is the value you want to set for each policy. You can view your current settings by typing Net accounts on its own.